Cyber security and digital government – wannacry or tangible reality?
Cyber security is now a global front page issue – events such as the #ecensusfail, alleged foreign government interference in political elections, and Wannacry has brought tremendous focus by the consumer, business and government of the risks of being online in an interconnected world.
Around the world businesses have been halted and government services interrupted.
We are increasingly seeing a symbiotic relationship between managing the cyber security threat and going digital. Indeed, I believe it is critical to overcoming the current challenges to “as a service” adoption – especially by government.
Today, we expect and demand to transact online, anywhere, anytime.
Wannacry and Petya (Goldeneye) attacks have really brought home the vulnerability that comes from living in an interconnected world. But the reality is that these attacks were exploiting a known vulnerability for which a patch had been published by Microsoft in March 2017.
ASD and digital government cyber security.
ASD has for years promoted simple steps that would have protected government, business and the public:
- Patch your systems.
- Back-up your data.
These are among the small handful of measures that have been shown by ASD to prevent over 80% of all cyber attacks. But, the reality is we clearly still struggle to do this ourselves.
There is a risk that the cyber security threat will become another excuse for delaying cloud adoption – especially in Government. On the positive side in recent years we are increasingly seeing an alignment of the stars that is building a groundswell of momentum for secure cloud adoption – particularly at a federal level in Australia.
The election of the Turnbull Government in 2016 has for the 1st time seen the appointment of both:
- A Minister for Digital Transformation – the Hon Angus Taylor;
- A Minister for Cyber Security – the Hon Dan Tehan
At a policy level, the concept of “Cloud First” is common across federal and state governments.
The establishment of the Digital Transformation Agency signalled a clear intention to make this agenda an integral part of the public service agenda. The DTA has taken over many procurement and policy functions from Finance. The DTA is currently working on a new Secure Cloud Strategy that is targeted for release later this year.
We are seeing some tangible evidence that momentum for a more secure cloud is finally happening.
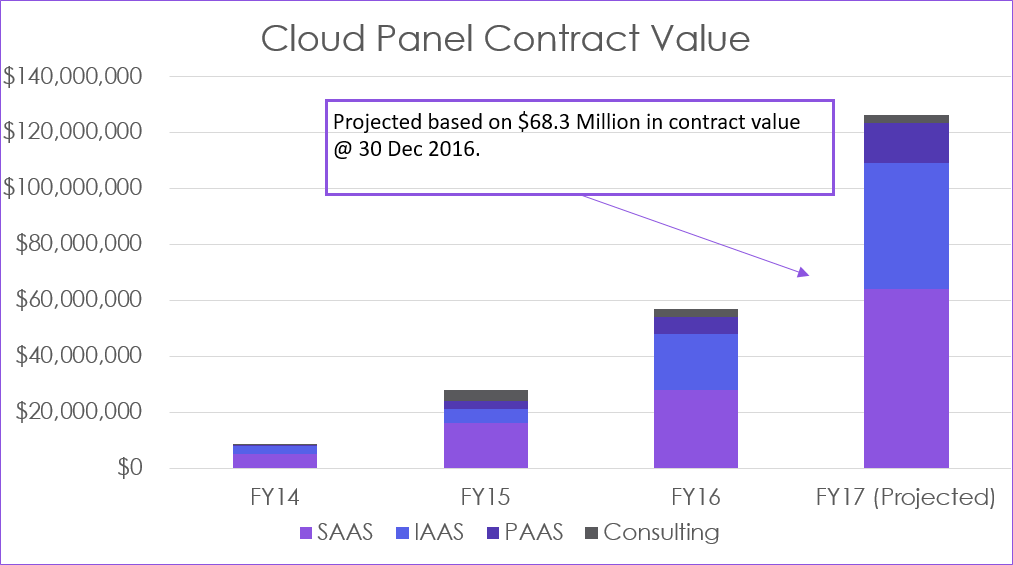
Figure 1: Macquarie Government highlighting the digital government cyber security and projected cloud spend trend.
Cloud spend has effectively been doubling annually – from a very low base. In the context of a $6 Billion plus pa federal ICT budget the reported contract values are still relatively small. The trend however is clear.
In the federal context, the Information Security Manual published by ASD mandates agencies to use cloud providers on the ASD approved Certified Cloud Services List. It should not be surprising that an assessment of published data by Intermedium shows that over 80% of the total contract value in FY2017 has gone to suppliers on the CCSL. This aligns to recommendations from the Government’s Review of the eCensus that called for security to be “baked in” in order to encourage digital transformation.
UK: digital government cyber security.
The UK Government experience is quite relevant to Australia.
The DTA has been modelled very closely on the UK Government Digital Service.
The GDS was supported not only by strong cloud first policies but also by both spend targets and commitment to award business to the SME market.
On study trips to the UK we learnt that UK agencies have largely developed a pragmatic strategy of moving to cloud, based on the characteristics of the specific application or workload. Existing virtualised workloads and new apps have been the first targets for moving to an “as a service” model. They provide the quick wins to show that the outcome works.
The large custom built legacy apps were often seen as too difficult to work with. The UK approach was to move these platforms to centralised government data centres until the application could be replaced.
In Australia, we are seeing a similar app by app approach in government. Again, new Apps that deliver a better digital experience and are designed to operate natively in the cloud are those that most easily encourage as-a-service adoption. It is critical when doing this, however, to take account of the security implications at the start – otherwise it can be a very costly exercise to try and do it when you look to go live in production.
Digital government cyber security – in summary.
- 1. Recent global attacks have brought home to all the risks of being online.
- 2. The cyber threat needs to be managed and baking in security is essential to overcoming the challenges to “as a service”;
- a. The risks cannot be ignored.
- b. Not just a problem for IT – is a challenge to be faced by all.
- c. Industry needs to do its part by demonstrating how their services are meeting the ISM.
- 3. Momentum is happening. Governments at all levels are making measurable progress in “as a service adoption”;
- a. At a federal level the CCSL is an enabler.
- b. Government can do more to make this process more transparent and clear.
- 4. There is no one right way. Experience shows us that the key is to get the right fit for the application. Sometimes this will be a hyper scale offering – other times it will be about delivering a more specialised outcome.
Derek Fittler
National Director, Government
Macquarie Government


