Beyond the Essential Eight (E8) – where to from here?

As the Australian government moves towards its next phase of the Cyber Security Strategy and consults industry to make legislative reforms, some quiet debate remains within government and industry circles about replacing the nation’s Essential Eight cyber mitigation strategies with some new framework, writes Aidan Tudehope.
It comes as Australia’s US allies push ahead with their revamped Cybersecurity Maturity Model Certification (CMMC) 2.0 program, with the new requirements to be a feature of relevant US government contracts from circa 2025.
Australia’s Essential Eight framework – or E8 as it’s colloquially known – is a baseline set of eight strategies to mitigate against the most common cyber security threats. Four maturity levels were added ranging from Zero to Three based on mitigating increasing sophisticated levels of adversary ‘tradecraft’, with Zero signifying easily exploited weaknesses, and Three signifying mitigation against sophisticated adversaries who adapt their tradecraft to compromise specific targets.
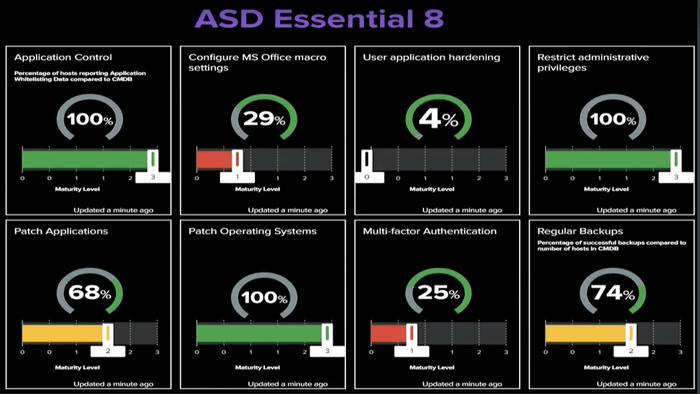
Federal Government agencies are now mandated to meet maturity level Two, mitigating against targeted attacks from more focused adversaries.
Meanwhile, state governments have taken a mixed approach though are broadly supportive of the E8 framework. The Victorian Government, for example, has its own Protective Data Security Framework (PSPF) which isn’t forced upon state agencies, but encouraged, and agencies that do adopt the framework are mandated to adopt E8 principles.
A mistake to go back to the drawing board.
While reflection on and even notable change to Australia’s E8 may be needed as we progress the Cyber Security Strategy and review key security acts such as Security of Critical Infrastructure (SOCI), replacing this important framework would be a major setback for a variety of reasons.
Firstly, the E8 – launched in 2017 – is not old by international standards. The makings of the CMMC, for instance, were first conceived in 2002.
Cybercriminals have evolved considerably since 2017 of course, but so too has the E8 model, for example with recent changes to the requirements shortening to 48 hours the timeframe to patch critical vulnerabilities on internet-facing endpoints and requiring phishing resistant multi-factor authentication methods at maturity level Two.

"While reflection on and even notable change to Australia’s E8 may be needed as we progress the Cyber Security Strategy and review key security acts … replacing this important framework would be a major setback for a variety of reasons."
Secondly, we speak to industry experts, government and enterprise CIOs and CISOs every day and the overwhelming view is that the E8 has held up as a strong baseline for organisations to work towards. A recent report also indicated 90 per cent of Australian enterprises are aligning their security programs to E8.
Thirdly, and most importantly, time is not on our side.
Cybercriminals are changing their approach and techniques, evolving their skills, and leveraging new tools such as artificial intelligence (AI) to keep ahead of our cyber defence efforts. If we were to go back to the drawing board to create some new framework, this could take years to design and implement across the economy to achieve a new baseline while cybercriminals continue to advance ahead.
The nature of cyber threat is such that our targets are changing all the time. Realistically, there’s no Nirvana point we can reach where organisations are as protected as they can be because threat actors are always working to circumvent that point.
Regulatory framework.
With this in mind, we could benefit from looking at E8 as more of a regulatory framework – an approach we constantly review, refine, iterate and educate on to ensure we’re staying on top of the latest trends and threats.
There are already plenty of changes we could introduce to better structure the E8 in this way, for example by expanding the focus from ‘endpoints’ (i.e., devices) to the network, the interconnecting layer between devices, their users and the internet.

Device protection is of course essential, but cybercriminals use networks to carry out attacks because the target surface area is much larger at that level than any one device. Our government security operations centre now monitors and intercepts between seven-to-eight billion network-based attacks every single day.
With the E8 positioned as the ‘how’, other regulatory instruments can step in place to define the ‘what’. For example, long-established state frameworks and – at a Federal Level – the industry-supported 2023-2030 Australian Cyber Security Strategy and revised SOCI Act, will fill that void.
With this regulatory approach in place, we can also start to think bigger and build communities of practice between likeminded government agencies that share similar threat environments. Portfolio clusters are the obvious place to start to build these communities as they share similar operating environments and cultures, serve similar purposes and, most importantly, share similar threat vectors and institutional knowledge where cyber security is concerned.
This could see Australia uplift its proactive cyber security capabilities, accelerate the speed of response, and strengthen defences to emerging threats.
It would also mean less doubling up, better knowledge sharing, and could help us achieve the overall higher level of cyber posture we need to become one of the world’s most secure nation by 2030.
First published on Government News