How NSW Government Agencies can meet Essential 8
The ACSC “Essential 8” is a set of IT strategies to establish baseline protection against cyber threats. Essential 8 cyber security is only the minimum subset of the ACSC’s Strategies to Mitigate Cyber Security Incidents – hence the “Essential” in its name. However, implementing them results in a significant cybersecurity posture uplift, preventing up to 85% of unauthorised intrusions.
All organisations – public and private – in Australia are encouraged to implement Essential 8. For NSW Government agencies, implementing Essential 8 is a policy imperative. Under the NSW Cyber Security Policy (CSP), each agency must implement Essential 8 (Section 3.2) as well as annually report a maturity assessment against Essential 8.
The Essential 8 Cyber Security Strategies.
The strategies are applied to how applications are accessed and executed, user authentication, administrator privileges and backups. The detailed list of strategies is available on the ACSC site, but in summary, they are:
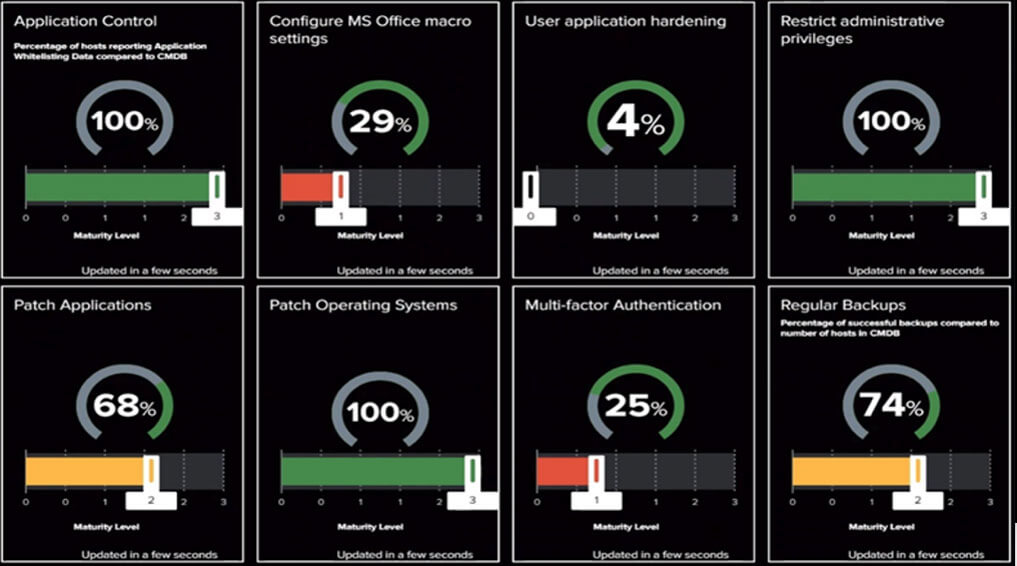
- Application Control: Restrict users from running anything except organisation-approved apps including executables (e.g.: “.exe files”), software libraries, control panel tools and HTML.
- Patch Applications: Keep applications updated to the latest versions, applying security patches within 2 weeks (or within 48 hours if a patch is in response to a known vulnerability.
- Configure Microsoft Office macro settings: Disable or limit the ability to execute VBA macros in Microsoft Word, Excel and other Microsoft Office apps. Macros are a common attack vector.
- User application hardening: Disable or limit the use of known exploited applications like Flash, Java, PDF and early versions of .NET framework.
- Restrict administrative privileges: Control the accounts that can make significant changes by validating every privilege escalation and restricting access of admin accounts to/from the internet.
- Patch operating systems: Applying patches (interim software upgrades) or vendor mitigations to operating systems and firmware. As with application patching, this should be completed within 2 weeks from release or within 48 hours for known exploits.
- Multi-factor authentication: Require all users accessing internet-facing or critical systems to provide a second factor that either they have (eg, a physical token, smartcard or software-based certificate) or are (eg, a fingerprint or iris scan).
- Regular Backups: Important data, applications and configurations are regularly backed up, Backup data is tested, and access is restricted to appropriate accounts only (e.g.: owner, backup administrators).
Maturity Levels.
The maturity levels are based in turn on the level of “adversary tradecraft” (i.e.: the sophistication of the threat actors and the tools they use) and targeting (i.e.: the level of threat faced by the agency).
The lowest of the three levels is suitable for small businesses. The highest should be implemented by critical infrastructure providers or organisations with a high threat level.
It allows agencies to prioritise deploying mitigation strategies to those assets most with the highest risk. As the strategies are designed to complement each other, agencies should implement all 8 to the same maturity level.
The Macquarie Government Essential 8 Dashboard.
Designed to give agencies real-time visibility of their Essential 8 compliance, Macquarie Government’s SOC and SIEM services include an Essential 8 dashboard that uses analysis of logs across agencies IT portfolio to determine the maturity level achieved against each Essential 8 cyber security strategy.
The dashboard not only lets agencies know where to direct implementation, but also help meet their CSP annual reporting obligations.